Industries > Cyber > Top 100 Cyber Security Companies: Ones to Watch in 2018
Top 100 Cyber Security Companies: Ones to Watch in 2018
Market Leaders And Innovative Disruptors in Cloud, Endpoint, Net, App, Data, Security Operations & Identification Management
• Do you need definitive Cyber Security industry analysis?
• Succinct cyber security company profiles?
• Technological insight?
• Clear competitor analysis?
• Actionable business recommendations?
Read on to discover how this definitive report can transform your own research and save you time.
The aim of the report is to provide an evaluation of the 100 significant major companies in the global Cyber Security industry by detailing their involvement in the market. The report does not claim to include every significant company involved within the market in 2018, but details the leading players showing the most potential within the cyber security market space.
If you want to be part of this growing industry, then read on to discover how this report could help you maximise your investment potential.
Report highlights
The report focuses on providing profiles of the leading and most innovative companies in the cyber security sector and analysing their role in the market and their cyber security based offerings This report aims to look at cyber security companies from an end user perspective.
The report will highlight the market overview, the leading 100 companies in the cyber security ecosystem & SWOT analysis of the cyber security market. The report is aimed at business executives who wish to gain an overview and information about the cyber security market’s leading companies’ landscape. We believe this will help our clients to understand the industry, technology, market segmentation and geographic breakdown, evaluate suppliers, and map potential usage to the available technologies. Our research will help you to understand the rapidly evolving cyber security market.
The report not only profiles the major cyber security companies such as
• Symantec
• Kaspersky lab
• McAfee
• VMWare
• TrendMicro
Plus major defence contractors benefitting from government cyber security contracts
• Lockheed Martin Corporation
• Raytheon
• BAE Systems PLC
• IBM
• Cisco Systems
But also 90 other smaller and innovative companies potentially disrupting the incumbents within the cyber security competitive landscape.
The report serves as a guide for Chief Executive Officers, Chief Information Officers, IT Analysts, Software Vendors, Small and Medium Businesses (SMBs), Large Enterprises, Software Developers, Cyber Security Executives, Cyber Security Market Players, and Service Providers to:
• Use as a guide for evaluating the potential of the Cyber Security market;
• Inform themselves about Cyber Security benefits and issues;
• Understand the provider landscape and the offerings;
• Anticipate potential IT development and opportunities in the Cyber Security market.
• Key questions answered
• What does the future hold for the cyber security industry?
• Where should you target your business strategy?
• Which applications should you focus upon?
• Which disruptive technologies should you invest in?
• Which companies should you form strategic alliances with?
• Which company is likely to success and why?
• What business models should you adopt?
• What industry trends should you be aware of?
• Target audience
• Leading cyber security companies
• Suppliers
• Contractors
• Technologists
• R&D staff
• Consultants
• Analysts
• CEO’s
• CIO’s
• COO’s
• Business development managers
• Investors
• Governments
• Agencies
• Industry organisations
• Banks
Visiongain is a trading partner with the US Federal Government
CCR Ref number: KD4R6
1. Executive Summary
1.1 Cyber Security Market Set to Take-off in 2018
1.2 Aim of the Report
1.3 Structure of the Report
1.4 Why You Should Read This Report
1.5 How This Report Delivers
1.6 Who is This Report For?
1.7 Methodology
1.8 About Visiongain
2. Introduction to the Cyber Security Market
2.1 Introduction to the Top 100 Cyber Security Companies
2.2 Assessing the Cyber Security Market Landscape
2.3 Overview of the Global Cyber Security Market
2.4 Defining the Global Cyber Security Market
2.5 Factors Driving Cyber Security’s Market Growth
2.6 Trend Analysis of the Cyber Security Market
2.7 Mechanisms of Cyber Attack
2.8 Types of Cyber Attack
2.9 Methods of Cyber Defence
2.10 List of Recent Cyber Security Attacks
3. Analysis of Leading Companies in the Global Cyber Security Ecosystem
3.1 Huge Potential for Growth in the Cyber Security Space
3.2 Assessing the Cyber Security Market Landscape
3.3 New Cyber Security Players Showing Potential to Disrupt Traditional Cyber Security Market
3.3.1 Shifting Expertise in the Cyber Security Market
3.3.2 Regional Breakdown of the Leading Companies in the Cyber Security Market
4. SWOT Analysis of the Cyber Security Market 2018
4.1 Strengths
4.2 Weaknesses
4.3 Opportunities
4.4 Threats
5. Top 100 Companies in the Cyber Security Market
5.1 Absolute Software Corporation
5.1.1 Absolute Software Corporation Cyber Security Overview
5.1.2 Absolute Software Recent Developments
5.1.3 Absolute Software Products and Service Offerings
5.1.4 Absolute Software Partnerships and Ventures
5.1.5 Absolute Software Future Outlook
5.2 Accuvant
5.2.1 Accuvant Cyber Security Overview
5.2.2 Accuvant Products & Solutions
5.3 Airbus Group
5.3.1 Airbus Group Cyber Security Overview
5.3.2 Airbus Group Cyber Security Products
5.3.3 Airbus Group Primary Market Competitors
5.3.4 Airbus Group Organisational Structure
5.4 Akamai Technologies Inc.
5.4.1 Akamai Technologies Inc. Cyber Security Overview
5.4.2 Akamai Technologies Recent Developments
5.4.3 Akamai Technologies Products and Services
5.4.4 Akamai Technologies Partnerships and Ventures
5.4.5 Akamai Technologies Future Outlook
5.5 AlienVault
5.5.1AlienVault Cyber Security Overview
5.6 AmazonWeb Services
5.6.1 Amazon Web Services Cyber Security Overview
5.6.2 AWS Recent Developments
5.6.3 AWS Products and Services
5.6.4 AWS Partnership and Ventures
5.6.5 AWS Future Outlook
5.7 Arbor Networks
5.7.1 Arbor Networks Cyber Security Overview
5.7.2 Arbor Networks Products & Services
5.8 Arxan Technology Inc.
5.8.1 Arxan Technology Inc. Cyber Security Overview
5.8.2 Arxan Technology Products & Services
5.9 AT&T
5.9.1 AT&T Cyber Security Overview
5.9.2 AT&T Recent Developments
5.9.3 AT&T Cyber Security Products and Services
5.9.4 AT&T Partnerships and Ventures
5.9.5 AT&T Future Outlook
5.10 AVG Technologies
5.10.1 AVG Technologies Cyber Security Overview
5.10.2 AVG Technologies Latest Developments
5.11 Avira
5.11.1 Avira Cyber Security Overview
5.11.2 Avira Recent Developments
5.11.3 List of Avira Products and Services
5.11.4 Avira Partnerships and Ventures
5.11.5 Avira Future Outlook
5.12BAE Systems
5.12.1 BAE Systems Cyber Security Overview
5.12.2 BAE Systems Primary Market Competitors
5.12.3 BAE Systems SWOT Analysis
5.13 Barracuda Networks
5.13.1 Barracuda Networks Cyber Security Overview
5.13.2 Barracuda Networks Products
5.14 Bay Dynamics
5.14.1 Bay Dynamics Cyber Security Overview
5.15 Bayshore Networks
5.15.1 Bayshore Networks Cyber Security Overview
5.15.2 Bayshore Networks Products
5.16 Berkley Varitronics
5.16.1 Berkley Varitronics Cyber Security Overview
5.16.2 Berkley Varitronics Products
5.16.3 Berkley Varitronics Customers
5.17 Bitdefender
5.17.1 Bitdefender Cyber Security Overview
5.17.2 Bitdefender Products
5.18 Boeing
5.18.1 Boeing Cyber Security Overview
5.18.2 Boeing Company Cyber Security Products
5.18.3 Boeing Company’s Primary Market Competitors
5.18.4 Boeing Company’s Regional Emphasis / Focus
5.18.5 Boeing Company’s M&A Activity
5.19 Booz Allen Hamilton
5.19.1Booz Allen Hamilton Cyber Security Overview
5.19.2 Booz Allen Hamilton, Inc. Cyber Security Market Products
5.19.3 Booz Allen Hamilton Cyber Security Contracts
5.19.4 Booz Allen Hamilton Primary Competitors
5.19.5 Booz Allen Hamilton, Inc.’s M&A Activity
5.20 Bromium
5.20.1 Bromium Cyber Security Overview
5.20.2 Bromium Products
5.21 BT
5.21.1 BT Cyber Security Overview
5.21.2 BT Recent Developments
5.21.3 BT Products and Services
5.21.4 BT Partnerships
5.21.5 BT Future Outlook
5.22Carbon Black
5.22.1 Carbon Black Cyber Security Overview
5.22.2 Carbon Black Products
5.23 Centrify
5.23.1 Centrify Cyber Security Overview
5.23.2 Centrify Recent Developments
5.23.3 Centrify Products and Services
5.23.4 Centrify Partnerships and Ventures
5.23.5 Centrify Future Outlook
5.24 CertainSafe
5.24.1 CertainSafe Cyber Security Overview
5.24.2 CertainSafe Solutions
5.25 Check Point
5.25.1 Check Point Cyber Security Overview
5.25.2 Check Point Primary Market Competitors
5.25.3 Check Point SWOT Analysis
5.26 Cisco Systems
5.26.2 Cisco Systems Cyber Security Overview
5.26.3 Cisco Systems Primary Market Competitors
5.26.4 Cisco Systems SWOT Analysis
5.27 Clearwater Compliance
5.27.1 Clearwater Compliance Cyber Security Overview
5.27.3 Clearwater Latest Developments
5.28 Coalfire
5.28.1 Coalfire Cyber Security Overview
5.28.2 Coalfire Cyber Security Offerings
5.29 Code42
5.29.1 Code42 Cybersecurity Overview
5.29.2 Code42 Recent developments
5.29.3 Code42Products and Services
5.29.4 Code42Partnerships and Ventures
5.29.5 Code42 Future Outlook
5.30 CodeDX
5.30.1 CodeDX Cyber Security Overview
5.30.2 CodeDX Products
5.31 Core Security
5.31.1 Core Security Cyber Security Overview
5.31.2 Core Security Products
5.32 Corero Network Security
5.32.1 Corero Network Security Cyber Security Overview
5.32.2 Corero Network Security Products
5.33 Cybera
5.33.1 Cybera Cybersecurity Overview
5.33.2 Cybera Recent Developments
5.33.3 Cybera Products and Services
5.33.4 Cybera Partnership and Ventures
5.33.5 Cybera Future Outlook
5.34 CyberArk
5.34.1 CyberArk Cyber Security Overview
5.34.2 CyberArk Products
5.35 Cyren
5.35.1 Cyren Cyber Security Overview
5.35.2 Cyren Products & Solutions
5.36 DB Networks
5.36.1 DB Networks Cyber Security Overview
5.36 DB Networks Products
5.37 Deep Instinct
5.37.1 Deep Instinct Cyber Security Overview
5.37.2 Solutions
5.38 Dell
5.38.1 Dell’s Vision for Connected Security
5.38.2 Dell Inc Competitors
5.38.4 Dell Inc Mergers and Acquisitions
5.39 Deloitte
5.39.1 Deloitte Cyber Security Overview
5.39.3 Deloitte Primary Market Competitors
5.39.4 Deloitte SWOT Analysis
5.40 Digital Shadows
5.40.1 Digital Shadows Cyber Security Overview
5.40.2 Digital Shadows Solutions
5.41 DXC Technology
5.41.1 DXC Recent Developments
5.41.2 DXC Products and services
5.41.3 DXC Partnerships and Ventures
5.41.4 DXC Future Outlook
5.42 Ernst & Young (EY)
5.42.1 EY Company Profile
5.42.3 EY Primary Market Competitors
5.42.4 EY SWOT Analysis
5.43 Easy Solutions
5.43.1 Easy Solutions Latest Developments
5.43.2 Solutions
5.44 F-Secure
5.44.1 F-Secure Cyber Security Overview
5.44.2 F-Secure Enterprise Security Solutions
5.45 Finjan Holdings
5.45.1 Finjan Holdings Cyber Security Overview
5.45.2 Finjan Holdings Security Products & Solutions
5.46 FireEye
5.46.1 FireEye Latest Developments
5.46.2 Challenges Faced By FireEye
5.47 Fluency Security
5.47.1 Fluency Security Cyber Security Overview
5.47.2 Fluency Security Products & Solutions
5.48 Fortinet
5.48.1 Fortinet Cyber Security Overview
5.48.3 Fortinet Primary Market Competitors
5.48.4 Fortinet SWOT Analysis
5.49 Gemalto
5.49.1 Gemalto Cyber Security Overview
5.49.2 Gemalto Products & Services
5.50 General Dynamics
5.50.1 General Dynamics Corporation’s Role in the Cyber Security Market
5.50.2 General Dynamics Corporation’s Organisational Structure
5.50.3 General Dynamics Corporation’s Cyber Security Products
5.50.4 General Dynamics Corporation’s Primary Market Competitors
5.50.6 General Dynamics Corporation’s Recent M&A Activity
5.51Herjavec Group
5.51.1 Overview of Herjavec’s Group Cyber Security Offerings
5.52 High-Tech Bridge
5.52.1 High-Tech Bridge Cyber Security Overview
5.52.2 High-Tech Bridge Products & Services
5.53 Honeywell
5.53.1 Honeywell Cyber Security Overview
5.53.2 Honeywell Strengths in Cyber Security
5.53.3 Honeywell Compliance with US Cyber Security Regulatory Standards
5.54Hewlett Packard
5.54.1 Hewlett Packard Company’s Role in the Cyber Security Market
5.54.2 Hewlett Packard Company’s Organisational Structure
5.54.3 Hewlett Packard Company’s Cyber Security Products
5.54.4 Hewlett Packard Company’s Primary Market Competitors
5.54.5 Hewlett Packard Company’s Recent M&A Activity
5.55 IBM Corporation
5.55.1 IBM Corporation Cyber Security Overview
5.55.2 IBM Latest Developments
5.55.3 IBM Primary Market Competitors
5.55.4 IBM SWOT Analysis
5.56 IT Security
5.56.1 IT Security Cyber Security Overview
5.56.2 IT Security Products & Services
5.57 Juniper Networks
5.57.1 Recent Developments
5.57.2 Juniper Networks Products and Services
5.57.3 Juniper Networks Partnerships and Ventures
5.57.4 Juniper Networks Future Outlook
5.58 Kaspersky Lab
5.58.1 Kaspersky Lab’s Role in the Cyber Security Market
5.58.2 Kaspersky Lab’s Organisational Structure
5.58.3 Kaspersky Lab’s Cyber Security Products
5.58.4 Kaspersky Lab’s Primary Market Competitors
5.58.5 Kaspersky Lab’s Recent M&A Activity
5.59 Kroll
5.59.1 Kroll Recent Developments
5.59.2 Kroll Products and Services
5.59.3 Kroll Partnerships and Ventures
5.59.4 Kroll Future Outlook
5.60 L3 Technologies
5.60.1 L3 Technologies Role in the Cyber Security Market
5.60.2 L3 Technologies Organisational Structure
5.60.3 L3 Technologies Holdings, Inc.’s Cyber Security Products
5.60.4 L3Communications Primary Competitors
5.60.5 L3 Technologies Recent M&A Activity
5.61Leidos
5.61.1LeidosRole in the Cyber Security Market
5.61.2Leidos Organisational Structure
5.61.3 Leidos Cyber Security Products
5.61.4LeidosPrimary Market Competitors
5.61.5LeidosRegional Emphasis / Focus
5.61.6 Leidos Recent M&A Activity
5.62Leonardo
5.62.1Leonardo’s Role in the Cyber Security Market
5.62.2 Leonardo Organisational Structure
5.62.3 Leonardo Cyber Security Products
5.62.4 Leonardo Primary Market Competitors
5.63 Lockheed Martin Corporation
5.63.1 Lockheed Martin Corporation Cyber Security Overview
5.63.2 Lockheed Martin Corporation Latest Developments
5.63.3Lockheed Martin Primary Market Competitors
5.63.4 Lockheed Martin SWOT Analysis
5.64 Malwarebytes
5.64.1 Malwarebytes Cyber Security Overview
5.64.2 Malwarebytes Products
5.65 McAfee LLC
5.65.1 McAfee Company Profile
5.65.1 McAfee Security Products
5.65.2McAfee Primary Market Competitors
5.65.3 McAfee SWOT Analysis
5.66 Mimecast
5.66.1 Mimecast Cyber Security Overview
5.66.2 Mimecast Products
5.67 MobileIron
5.67.1 MobileIron Inc. Cyber Security Overview
5.67.2 MobileIron Products
5.68 Netskope
5.68.1 Netskope Cyber Security Overview
5.68.2 Netskope Products & Solutions
5.69 Nexusguard
5.69.1 Nexusguard Recent Developments
5.69.2 Nexusguard Products and Services
5.69.3 Nexusguard Partnerships and Ventures
5.69.4 Nexusguard Future Outlook
5.70 Northrop Grumman Corporation
5.70.1 Northrop Grumman Corporation’s Role in the Cyber Security Market
5.70.2 Northrop Grumman Corporation’s Organisational Structure
5.70.3 Northrop Grumman Corporation’s Cyber Security Products
5.70.4 Northrop Grumman Corporation’s Primary Market Competitors
5.70.5 Northrop Grumman Corporation’s Recent M&A Activity
5.71 Optiv
5.71.1 Optiv Cyber Security Overview
5.71.2 Optiv Products & Solutions
5.72 Palantir Technologies
5.72.1 Palantir Technologies Cyber Security Overview
5.72.2 Palantir Technologies Products
5.73 Palo Alto Networks
5.73.1 Palo Alto Networks Latest Developments
5.74 Panda Security
5.74.1 Panda Security Recent Developments
5.74.2 Panda Security Products and Services
5.74.3 Panda Security Partnerships and Ventures
5.74.4 Panda Security Future Outlook
5.75 Patriot One Technologies
5.75.1 Patriot One Technologies Cyber Security Overview
5.76 Pindrop Security
5.76.1 Pindrop Security Cyber Security Overview
5.76.2 Pindrop Cyber Security Services
5.76.3 Pindrop Security Research & Development
5.77 Ping Identity
5.77.1 Ping Identity Cyber Security Overview
5.77.2 Ping Identity Products
5.78 Proofpoint
5.78.1 Proofpoint Cyber Security Overview
5.78.2 Proofpoint Solutions
5.79 PWC
5.79.1 PWC Cyber Security Overview
5.79.2 PWC Primary Market Competitors
5.79.3 PWC SWOT Analysis
5.80 Qualys
5.80.1 Qualys Cyber Security Overview
5.80.2 Qualys Products
5.81 Radware
5.81.1 Radware Cyber Security Overview
5.81.2 Radware Solutions
5.82 Raytheon Company
5.82.1 Raytheon Company Cyber Security Overview
5.82.2 Raytheon Primary Market Competitors
5.82.3 Raytheon SWOT Analysis
5.83 RUAG Cyber Security
5.83.1 RUAG Cyber Security Overview
5.83.2 RUAG Solutions
5.84 SecuEra
5.84.1 SecuEra Cyber Security Overview
5.84.2 SecuEra Products
5.85 Sera-Brynn
5.85.1 Sera-Brynn Cyber Security Overview
5.85.2 Sera-Brynn Services
5.86 Sophos
5.86.1 Sophos Recent Developments
5.86.2 Sophos Products and Services
5.86.3 Sophos Partnerships and Ventures
5.86.4 Sophos Future Outlook
5.87 Splunk
5.87.1 Splunk Cybersecurity Overview
5.87.2 Splunk Recent Developments
5.87.3 Splunk Products and Services
5.87.4 Splunk Partnerships
5.87.5 Splunk Future Outlook
5.88 Symantec Corporation
5.88.1 Symantec Company Profile
5.88.2 Symantec Primary Market Competitors
5.88.3 Symantec SWOT Analysis
5.89 Tanium
5.89.1 Tanium Cyber Security Overview
5.89.2 Tanium Products & Solutions
5.90 Templar Shield
5.90.1 Templar Shield Cyber Security Overview
5.90.2 Templar Shield Services
5.91Thales Group
5.91.1 Thales Group’s Role in the Cyber Security Market
5.91.2 Thales Group’s Organisational Structure
5.91.3 Thales Group’s Cyber Security Products
5.90.4Thales Group’s Primary Market Competitors
5.91.5 Thales Group’s Regional Emphasis / Focus
5.91.6 Thales Group’s M&A Activity
5.92 Trend Micro
5.92.1 Trend Micro Role in the Cyber Security Market
5.92.2 Trend Micro Organisational Structure
5.92.3 Trend Micro Cyber Security Products
5.92.4 Trend Micro, Inc.’s Recent M&A Activity
5.92.5 Trend Micro SWOT Analysis
5.93 Tripwire
5.93.1 Tripwire Cyber Security Overview
5.93.2 Tripwire Industry Solutions
5.94 Ultra Electronics
5.94.1 Ultra Electronics Role in the Cyber Security Market
5.94.2 Ultra Electronics Organisational Structure
5.94.3 Ultra Electronics Cyber Security Products
5.94.4 Ultra Electronics Primary Market Competitors
5.94.5 Ultra Electronics Regional Emphasis / Focus
5.95 vArmour
5.95.1 vArmour Recent Developments
5.95.2 vArmour Products and Services
5.95.3 vArmour Partnerships and Ventures
5.95.4 vArmour Future Outlook
5.96 Veracode
5.96.1 Veracode Latest Developments
5.97 Virtual Armour
5.97.1 Virtual Armour Cyber Security Overview
5.97.2 Virtual Armour Products & Solutions
5.98 VMWare
5.98.1 VMWare Cyber Security Overview
5.98.2 VMWare Products
5.98.4 VMware Future Outlook
5.99 Watch Guard
5.99.1 Watch Guard Recent Developments
5.99.2 Watch Guard Products and services
5.99.3 Watch Guard Partnerships and Ventures
5.99.4 Watch Guard Future Outlook
5.100 Webroot
5.100.1 Webroot Recent Developments
5.100.2 Webroot Products and Services
5.100.3 Webroot Partnerships and Ventures
5.100.4 Webroot Future Outlook
6. Conclusions
6.1 Why Will the Cyber Security Market Continue to Grow?
6.2 Large Players Struggling to Maintain Top Position
6.3 Cyber Security a Vital to National Defence
6.4 Increasing Number of Cyber Attacks on Businesses
6.5 Analysing the Future Outlook of the Cyber Security Market
7. Glossary
List of Tables
Table 2.1 Mechanisms of Cyber Attack (Type, Description)
Table 2.2 Types of Cyber Attack (Type, Description)
Table 2.3 Cyber Defence Systems (Method of Cyber Defence, Description)
Table 2.4 Recent History of High Profile Cyber Attacks (Date, Description)
Table 4.1 SWOT Analysis of the Global Cyber Security Market 2018
Table 5.1 Accuvant Cyber Security Services
Table 5.2 Airbus Group Cyber Security Products / Services (Company Section, Product, Key Features)
Table 5.3 Arxan Industry Services
Table 5.4 Recent BAE Systems Cyber Security Contracts / Projects / Programmes (Date, Country, Value ($m), Details)
Table 5.5 BAE Systems Selected Cyber Security Products & Services (Company Division, Product, Specification)
Table 5.6 SWOT Analysis of BAE Systems 2018
Table 5.7 Barracuda Cyber Security Solutions
Table 5.8 Bayshore Networks Cyber Security Industry Usage
Table 5.9 Boeing Company Cyber Security Products / Services (Company Section, Product, Specifications)
Table 5.10 Booz Allen Hamilton, Inc. Cyber Security Products / Services (Company Section, Product, Specifications)
Table 5.11 Recent Booz Allen Hamilton, Inc. Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.12 Bromium Cyber Security Industry Solutions
Table 5.13 Carbon Black Cyber Security Solutions
Table 5.14 CertainSafe Cyber Security Industry Services
Table 5.15 Check Point Selected Cyber Security Products & Services (Product, Specification)
Table 5.16 SWOT Analysis CheckPoint 2018
Table 5.17 Recent Cisco Systems Cyber Security Contracts / Projects / Programmes (Date, Country, Value ($m), Details)
Table 5.18 Cisco Systems Selected Cyber Security Products (Product/Service Name, Specification)
Table 5.19 SWOT Analysis of Cisco Systems 2018
Table 5.20 Core Security Industry Solutions
Table 5.21 Corero Network Cyber Security Solutions
Table 5.22 Dell Inc Selected Cyber Security Products & Services 2018 (Company Division, Product, Specification)
Table 5.23 Deloitte Selected Cyber Security Products & Services 2018(Product, Specification)
Table 5.24 SWOT Analysis of Deloitte, 2018
Table 5.25 EY Selected Cyber Security Products & Services (Product, Specification)
Table 5.26 SWOT Analysis of EY 2018
Table 5.27 F-Secure Cyber Security End User Products
Table 5.28 Fortinet Major Cyber Security Product Launches/ Enhancements (Date, Country, Value ($m), Details)
Table 5.29 Fortinet Selected Cyber Security Products & Services (Product, Specification)
Table 5.30 SWOT Analysis of Fortinet, 2018
Table 5.31 Recent General Dynamics Corporation Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.32 General Dynamics Corporation’s Cyber Security Products / Services (Company Section, Product, Specifications)
Table 5.33 Herjavec’s core managed security services
Table 5.34 Recent Hewlett Packard Company Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.35 Hewlett Packard Company’s Cyber Security Products / Services (Company Section, Product, Specifications)
Table 5.36 Recent IBM Cyber Security Contracts / Projects / Programmes (Date, Country, Value ($m), Details)
Table 5.37 IBM Corporation Cyber-security (Product/Service Type, Company Division, Product/Service Name, Specification)
Table 5.38 SWOT Analysis of IBM 2018
Table 5.39 IT Security Cyber Security Services
Table 5.40 Kaspersky Lab’s Cyber Security Products / Services (Company Section, Product, Key Features)
Table 5.41 Recent L3 Technologies Holdings, Inc. Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.42 L3 Technologies Holdings, Inc.’s Products / Services (Company Section, Product, Specifications)
Table 5.43 Recent Leidos Cyber Security Contracts / Projects / Programmes (Date, Country, Value, Details)
Table 5.44 Leidos, Inc.’s Cyber Security Products / Services (Company Section, Product, Key Features)
Table 5.45 Finmeccanica Products / Services (Company Section, Product, Specification)
Table 5.46 Lockheed Martin Corporation Cyber Security Contracts & Programmes 2010-2017 (Date, Country, Value ($m), Details)
Table 5.47 Lockheed Martin Selected Cyber Security Products & Services 2018 (Product, Specification)
Table 5.48 SWOT Analysis of Lockheed Martin 2018
Table 5.49 McAfee Selected Cyber Security Products & Services 2018 (Product, Specification)
Table 5.50 SWOT Analysis of McAfee 2018
Table 5.51 MobileIron Cyber Security Solutions
Table 5.52 Recent Northrop Grumman Corporation Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.53 Northrop Grumman Corporation’s Cyber Security Products / Services (Company Section, Product, Specifications)
Table 5.54 PinDrop Security Partners
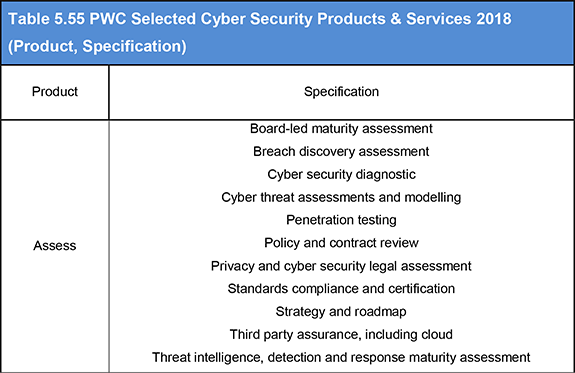
Table 5.55 PWC Selected Cyber Security Products & Services 2018(Product, Specification)
Table 5.56 SWOT Analysis of PwC 2018
Table 5.57 Qualys Latest Cyber Security Products
Table 5.58 Raytheon Company Major Cyber Security Contracts & Programmes (Date, Country, Value ($m), Details)
Table 5.59 Raytheon Company Selected Cyber Security Products & Services (Company Division, Product, Specification)
Table 5.60 SWOT Analysis of Raytheon, 2018
Table 5.61 Symantec Corporation Selected Cyber Security Products & Services (Product)
Table 5.62 SWOT Analysis of Symantec, 2018
Table 5.63 Templar Shield Cyber Security Services
Table 5.64 Recent Thales Group Cyber Security Contracts / Projects / Programmes (Date, Country, Value $m, Details)
Table 5.65 Thales Group’s Cyber Security Products / Services (Company Section, Product, Key Features)
Table 5.66 Trend Micro Cyber Security Products / Services (Company Section, Product, Key Features)
Table 5.67 SWOT Analysis of Trend Micro 2018
Table 5.68 TripWire Cyber Security Products
Table 5.69 Ultra Electronics Holdings plc’s Cyber Security Products / Services (Company Section, Product, Specifications)
List of Figures
Figure 5.1 Airbus Group Organizational Structure
Figure 5.2 Arbor Products and Services
Figure 5.3 BAE Systems Organizational Structure of Cyber Security
Figure 5.4 BAE Systems Primary Market Competitors
Figure 5.5 Boeing Company’s Regional Emphasis/Focus
Figure 5.6 CheckPoint Primary Market Competitors
Figure 5.7 Cisco Systems Organizational Structure of Cyber Security Divisions
Figure 5.8 Cisco Systems Primary Market Competitors
Figure 5.9 Dell Inc. Organizational Structure
Figure 5.10 Deloitte Organizational Structure 2018
Figure 5.11 Deloitte Primary Market Competitors
Figure 5.12 DXC Products & Services
Figure 5.13 EY Organizational Structure 2018
Figure 5.14 EY Primary Market Competitors 2018
Figure 5.15 Fortinet Organizational Structure of Cyber Security Divisions
Figure 5.16 Fortinet Primary Market Competitors 2018
Figure 5.17 General Dynamics Corporation’s Organizational Structure
Figure 5.18 Hewlett Packard Company’s Organizational Structure
Figure 5.19 IBM Organizational Structure of Cyber Security Divisions
Figure 5.20 IBM Primary Market Competitors
Figure 5.21 Kaspersky Lab’s Organizational Structure
Figure 5.22 L3 Technologies Organizational Structure
Figure 5.23 Leidos Organizational Structure
Figure 5.24 Leidos, Inc.’s Regional Emphasis / Focus (Region)
Figure 5.25 Leonardo S.p.A.’s Organizational Structure
Figure 5.26 Lockheed Martin Organisational Structure of Cyber Security Divisions
Figure 5.27 Lockheed Martin Primary Competitors
Figure 5.28 McAfee Primary Market Competitors 2018
Figure 5.29 Northrop Grumman Corporation’s Organisational Structure
Figure 5.30 PwC Organisational Structure of Cyber Security Divisions
Figure 5.31 PwC Primary Market Competitors 2018
Figure 5.32 Raytheon Organisational Structure of Cyber Security Divisions
Figure 5.33 Raytheon Primary Market Competitors 2018
Figure 5.34 Sophos Cyber Security Offerings
Figure 5.35 Symantec Organisational Structure of Cyber Security Divisions
Figure 5.36 Symantec Primary Market Competitors
Figure 5.37 Thales Group Organizational Structure
Figure 5.38 Thales Group’s Regional Emphasis/ Focus (Region)
Figure 5.39 Trend Micro Organizational Structure
Figure 5.40 Ultra Electronics Organizational Structure
Figure 5.41 Ultra Electronics Regional Emphasis/ Focus (Region)
Figure 5.42 vArmour’s Cyber Security Offerings
Figure 5.43 Watch Guard Data Loss Prevention and Automated Intelligence and Decision Making Framework
Figure 5.44 Webroot Products
Absolute Software Corporation
Accenture
ActivIdentity
Adaptive Methods
Adobe Systems
Advatech Pacific Inc
Agnitio
Airbus Defence & Space
Airbus Group SE
Akamai Cloud Security Solutions
Akamai Technologies, Inc.
Alfresco
AlienVault
Allianz
Amazon Web Services
Anthem
Aon
Apcon
AppAssure.
Apple, Inc.
Arbor Networks
Argon ST
Arkoon Network Security
Arturai
AT&T Inc
Aurora Flight Sciences
Autodesk
Avast
Avaya Devconnect
AVG Technologies
Avira Operations GmbH & Co. KG
AWS Security Services
BA Internet Solutions
BAE Intelligence and Security
BAE Systems Applied Intelligence
BAE Systems plc
Bain & Co
Barclays Bank
Barracuda Networks, Inc
Bay Dynamics
Bayshore Networks, LLC
Belden Inc
Berkeley Varitronics
Bitdefender
Blue Coat
Boeing Capital
Boeing Commercial Airplanes (BCA)
Boeing Company
Boeing Cyber Engagement Center (CEC)
Boeing Defense, Space & Security (BDS)
Boeing Information Solutions
Boeing Shared Services Group
Booz Allen Hamilton, Inc.
Boston Consulting Group (BCG)
Box
Bromium
BT Group plc
CACI International
Canonical
Carbon Black
Cassidian Cybersecurity
CDN Solutions
Centrify Corporation
CertainSafe
Check Point Software Technologies Ltd
China Telecom Cloud Computing Corporation
Cisco Security Group
Cisco Systems, Inc.
Clavister
Clearswift
Clearwater Compliance
Cloudera
Cloudflare
Coalfire
Code DX
Code42
Cognizant Technology Solutions
Computer Sciences Corporation (CSC)
Conexsys
Contact Solutions
Contrail Security
Core Security
CoreLabs
Corero Network Security, Inc
Credant Technologies.
Crossbeam
Crowdstrike.
CYAN Networks
Cybera
CyberArk
Cyphort
Cyren
DarkMatter
DB Networks
Decision Lab
Deep Instinct
Deep Root Analytics
Dell Federal Systems LP
Dell Inc.
Dell SecureWorks
Deloitte Consulting LLP
Deutsche Telekom AG
Diebold Nixdorf
Dolby
DRS Technologies Inc
DXC Technology
Easy Solutions
Elderwood Group,
Eletrobras
EMC Corporation
Engility Holdings, Inc.
Eurocopter
Expedia
EY
F5
FedEx
Finjan Blue, Inc.
Finjan Holdings
Finjan Mobile, Inc.
Finjan, Inc.
Finmeccanica S.p.A.
FireEye, Inc.
FluencySecurity
Follett
Forcepoint
Fortinet, Inc.
F-Secure Corporation
Fujitsu
GE
Gemalto
Genentech
General Dynamics Corporation
Genesys
Global Technical Systems
Google
Guidance Software
Gulfstream Aerospace.
Hastings Direct
HCL Comnet
Herjavec Group
Hewlett-Packard (HP)
High-Tech Bridge
HP Enterprise Services (HPE)
Huawei
IBM Corporation
IBM Security
IDolody
Incedo
Infosys, Optiv
Insight Technology, Inc.,
Intel Corporation
intelligence AG
InterContinental Hotels Group
Ionic Security
IPC
IT Security
Jones & Frank
JP Morgan Chase
Juniper Networks
KACE Networks
Kaspersky Lab
Keypoint Government Solutions
Kollmorgen Electro-Optical
KPMG
Kroll
L-3 Communications
L-3 Communications Holdings, Inc.
L3 Technologies Holdings, Inc.
Lastline
Leidos
Lenovo
Leonardo
Level 3
LinkedIn
Lockheed Martin Corporation
Lockheed’s Global Services and Information Systems
Maersk
Malwarebytes
Mandiant
McAfee LLC
McAfee, Inc.
Microsoft Corporation
Microsoft Partner
Mimecast
Mitsubishi Heavy Industries (MHI)
MobileIron Inc.
Morgan Advanced Materials PLC
Morphick, Inc.
MPC
NASDAQ
National Geographic
NBC Sports Group
NCP engineering
Netasq
Netflix
Netskope
New York Times
Nexusguard
Northrop Grumman Corporation.
Novell
NTT
O2
Okta
OPSWAT
Optiv
Oracle/Sun
Orbital ATK
PA Consulting
Palantir Technologies, Inc
Palo Alto Networks Inc.
Panda Security
Patriot One Technologies
Percipient Networks
Perot Systems
Ping Identity
Primera Blue Cross
Proofpoint, Inc.,
PwC
QRadar
Qualcomm
Qualys
Quest Software
Rackspace
Radware
Raytheon Company
Raytheon Intelligence and Information Systems
Raytheon SI Government Solutions Inc
Red Canary
Ricardo
Roche
Rosneft
RSA Security
RUAG Cyber Security
Saudi Aramco
Science Applications International Corporation (SAIC),
SecuEra
Securecast
SecureWorks Inc
Security Compass
SELEX ES
SENGEX
Sera-Brynn, LLC
Serco Inc.
Shell
SignalSense
SkyHigh Networks
Sonian
SonicWall Inc.
Sony Corporation
Sony Pictures Entertainment
Sophos Ltd.
Sourcefire, Inc.
Spartan
SpeechPro
Splunk
Sqrrl Data
SRA International
SurfEasy
Symantec Corporation
Synergy Systems
Synnex
Tanium
Target
Taringa
Tasc Inc
Tata Communications
Tech Mahindra
Telco Systems
Telstra
Texas Hospital Association
Thales Group
Thoma Bravo
Toshiba
TrendMicro, Inc.
Tripwire, Inc.
True North Automation
Tumblr
TV5Monde
Twitter
Uber
Ultra Electronics Holdings
Unicredit
Unisys
vArmour
Vector
Vencore Holding Corp.
Veracode
Verizon
Vigilant
Virtual Armour
VK.com
VMware
Warburg Pincus
Watch Guard
Webroot
Websense
Wipro
WPP
X15 Software
Yahoo
YTN
Zimperium
Zurich Insurance
Zurich Ireland
Organisations mentioned
Applied Computer Security Associates (ACSA)
Bank of England
CBEST
Cloud Security Alliance (CSA)
Computing Research Association's Committee on the Status of Women in Computing Research (CRA-W)
DARPA
Defence Research and Development Organisation (DRDO)
Defense Intelligence Agency
Defense Threat Reduction Agency (DTRA)
Department of Homeland Security
Estonian Ministry of Defense
Federal Bureau of Investigation (FBI)
HIPAA
Indo-Tibetan Border Police (ITBP)
INTERPOL
ISA Security Compliance Institute (ISCI)
Joint IED Defeat Organisation
Ministry of External Affairs
Ministry of Home Affairs
NASA
National Security Agency (NSA)
NATO
NCSC
NIST
People’s Liberation Army (PLA)
Redstone Arsenal
Sandia National Laboratories
Security Industry Association
Singapore’s INTERPOL Global Complex for Innovation (IGCI)
SOC
UK Highways Agency
UK MOD
UK Skills Funding Agency
US Air Force
US Air Force Research Laboratory (AFRL)
US Army Regional Cyber Center-Europe, 5th Signal Command
US Central Intelligence Agency (CIA)
US Department of Defense
US Department of Defense (DoD)
US Department of Defense Chief Information Office
US Department of Homeland Security
US Department of Justice
US DOD Manpower Data Centre
US Government’s Office of Personnel Management (OPM
US Marine Corps (USMC)
US Marine Corps Enterprise Network
US National Reconnaissance Office
US Navy (USN)
US Navy Information Dominance Force’s Shore Modernization and Integration Directorate
US. Navy
World Anti-Doping Agency
World Bank
Download sample pages
Complete the form below to download your free sample pages for Top 100 Cyber Security Companies: Ones to Watch in 2018
Related reports
-

Connected Aircraft Market Report 2018-2028
Industry professionals: cut through media hype and exaggeration by reading an objective dispassionate Visiongain report on the connected aircraft market....
Full DetailsPublished: 22 May 2018 -

Industrial Internet of Things (IIoT) Market Report 2018-2028
Visiongain has produced an in-Depth market research report studying the Industrial Internet of Things, analysing the rapid growth of this...
Full DetailsPublished: 01 May 2018 -

Automotive Cyber Security Market Report 2018-2028
The Automotive Cyber Security Market Report 2018-2028: evaluates the market drivers and technological solutions essential to the protection of the...
Full DetailsPublished: 18 June 2018 -

Internet of Things (IoT) Market Report 2018-2028
The latest report from business intelligence provider Visiongain offers comprehensive analysis of the global Internet of Things market. Visiongain assesses...
Full DetailsPublished: 13 April 2018 -

Aviation Cyber Security Market Forecast 2017-2027
Developments in aviation cyber security have had a significant impact on the wider aviation and cyber security markets. Visiongain’s report...
Full DetailsPublished: 31 July 2017 -

Cyber Insurance Market Report 2017-2027
Our 164-page report provides 113 tables, charts, and graphs. Read on to discover the most lucrative areas in the industry...
Full DetailsPublished: 30 October 2017 -

Next Generation Cyber Security Market Report 2018-2028
The latest report from business intelligence provider visiongain assesses that the global Next Generation Cyber Security market is expected to...
Full DetailsPublished: 21 August 2018 -

Artificial Intelligence in Cyber Security World Market to 2027
Where is the Artificial Intelligence in Cyber Security market heading? If you are involved in this sector you must read...
Full DetailsPublished: 08 December 2017 -

Wearable Technology Market 2018-2028
Our 172-page report provides 134 tables, charts, and graphs. Read on to discover the most lucrative areas in the industry...
Full DetailsPublished: 16 January 2018 -

Cyber Security Market Report 2018-2028
The latest report from business intelligence provider Visiongain offers comprehensive analysis of the global Cyber Security market. Visiongain assesses that...
Full DetailsPublished: 13 July 2018
Download sample pages
Complete the form below to download your free sample pages for Top 100 Cyber Security Companies: Ones to Watch in 2018
Do you have any custom requirements we can help you with?
Any specific country, geo region, market segment or specific company information?
Email us today, we can discuss your needs and see how we can help: jamie.roberts@visiongain.com
Would you like a free report overview of the report of your choice?
If so, please drop an email to Jamie Roberts stating your chosen report title to jamie.roberts@visiongain.com
Visiongain cyber reports are compiled using a broad and rich mixture of both primary and secondary information to produce an overall industry outlook. In order to provide our clients with the best product possible product, Visiongain analysts reach out to market-leading vendors and industry experts but also review a wealth of financial data and product information from a vast range of sources. To find out more about our reports methodology, please email jamie.roberts@visiongain.com
“A quick thanks for the IoT Security Report 2021 received yesterday. It’s well put together and just what I wanted. The whole buying process was quick, as was the delivery. I’ll definitely buy more from Visiongain. Good price too.”
Jack Schuster, Intertek
Latest Cyber news
Quantum Sensors Market
The global Quantum Sensors market is projected to grow at a CAGR of 15.3% by 2034
10 June 2024
Quantum Communication Market
The global Quantum Communication market is projected to grow at a CAGR of 25.7% by 2034
05 June 2024
Predictive Analytics Market
The global predictive analytics market was valued at US$13.69 billion in 2023 and is projected to grow at a CAGR of 21.7% during the forecast period 2024-2034.
29 May 2024
Cloud Security Market
The global Cloud Security market was valued at US$41.15 billion in 2023 and is projected to grow at a CAGR of 12.7% during the forecast period 2024-2034.
24 May 2024

















